Also, harmonizing regulations and response frameworks would make improvements to coordination and collaboration efforts. Harmonization would let for relieve of collaboration across jurisdictions, pivotal for intervening while in the compact windows of chance to get back stolen resources.
Some cryptocurrencies share a blockchain, though other cryptocurrencies work by themselves individual blockchains.
Supplemental safety steps from either Harmless Wallet or copyright might have lessened the likelihood of the incident happening. By way of example, employing pre-signing simulations might have allowed personnel to preview the destination of a transaction. Enacting delays for giant withdrawals also would have supplied copyright time to overview the transaction and freeze the resources.
A lot of argue that regulation productive for securing banking companies is fewer helpful in the copyright space because of the business?�s decentralized nature. copyright requirements much more safety polices, but In addition it requires new methods that take note of its dissimilarities from fiat money establishments.
If you need aid acquiring the page to begin your verification on cell, faucet the profile icon in the very best appropriate corner of your private home web page, then from profile decide on Id Verification.
This tactic seeks to overwhelm compliance analysts, regulation enforcement, and blockchain analysts by executing A large number of transactions, both of those by DEXs and wallet-to-wallet transfers. After the costly initiatives to hide the transaction 바이비트 path, the last word objective of this method will likely be to convert the cash into fiat currency, or forex issued by a authorities such as US greenback or the euro.
These risk actors were then capable to steal AWS session tokens, the temporary keys that enable you to ask for short term qualifications for your employer?�s AWS account. By hijacking Lively tokens, the attackers were capable to bypass MFA controls and gain entry to Harmless Wallet ?�s AWS account. By timing their attempts to coincide Along with the developer?�s regular operate several hours, Additionally they remained undetected until eventually the actual heist.}
 Jaleel White Then & Now!
Jaleel White Then & Now! Marques Houston Then & Now!
Marques Houston Then & Now! Michael C. Maronna Then & Now!
Michael C. Maronna Then & Now!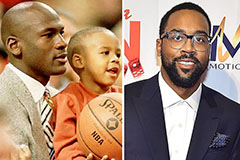 Marcus Jordan Then & Now!
Marcus Jordan Then & Now!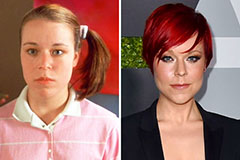 Tina Majorino Then & Now!
Tina Majorino Then & Now!